You may have heard the term OSINT(“Open Source Intelligence”) The basics is that you can use public sources to get information about a target during your recon.
There are many tools that are available to perform this task such as Google, Maltego, SHODAN etc,
one of the tools that really puts a perspective not only on what can be found but just how insecure some devices are.
Meet SHODAN https://www.shodan.io/
Shodan was created as a search engine for devices for example if you search “DLINK” you will find all of the Dlink routers and devices found by the crawler. The crawler looks for devices with publically reachable ports such as HTTP or Telnet.
You can also search by service type such as DNS and you will see all devices that have port 53 open lets take a look.
Here is the SHODAN main page you can perform some basic searches without a login but you will need an account for full site access
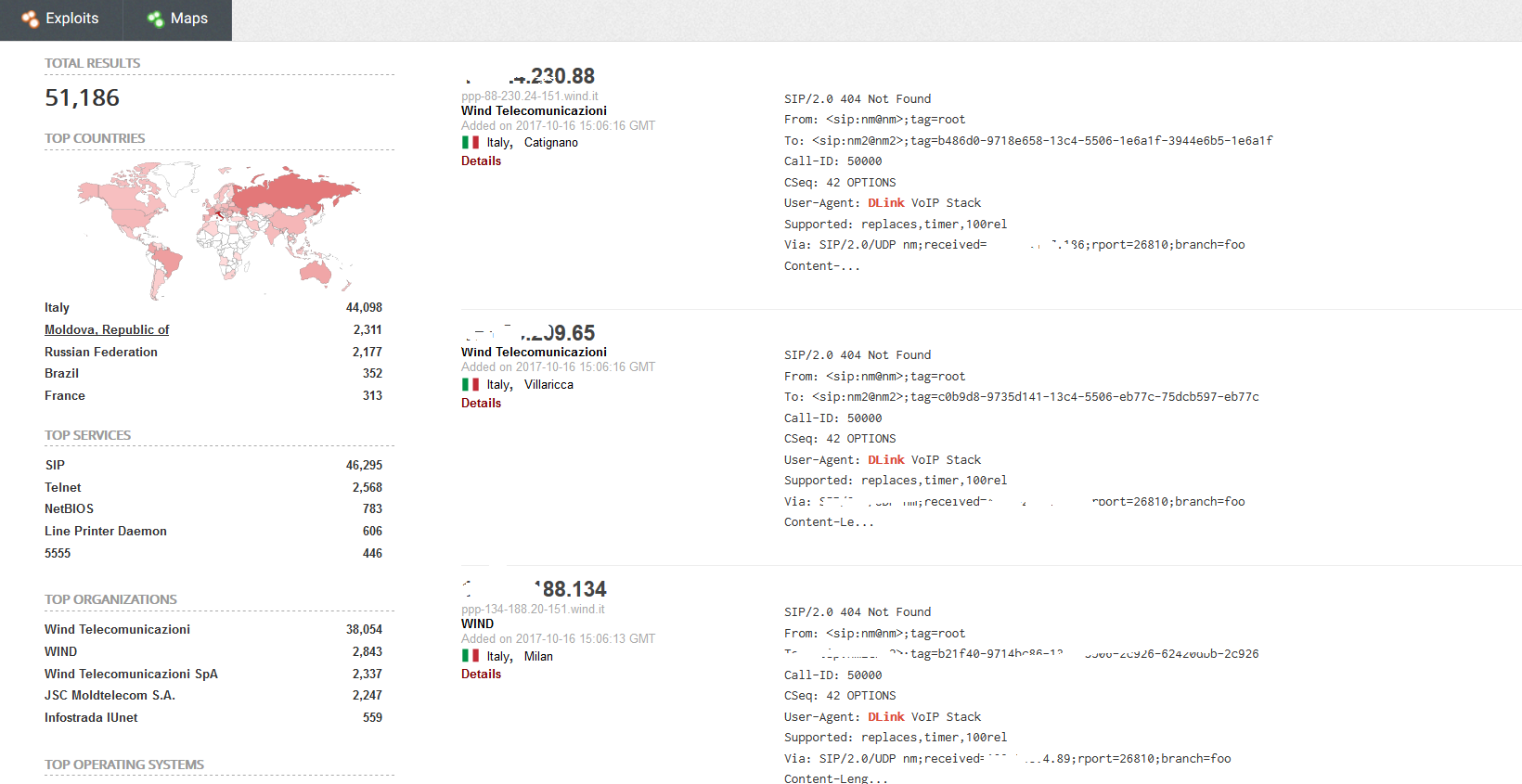
A search on Dlink devices brings up the following results I have removed the IP’s
As you can see from above the search engine has found some services on these devices that are exposed to the internet lets drill down on one of them to see what the results are
As you can see from above the device has NTP exposed to the internet a big NONO as we are aware NTP is used in a lot of DDoS attacks.
You can get creative with your searches I am not going to do that in this article but you can take some time to explore the tool.
This tool sheds a lot of light on the issues that are facing this industry a lot of consumer devices and even corporate devices improperly configured and exposing these services to the internet.
Whats more is that some of these devices still have the default credentials !!!!
Let me know what you think about this tool
Sean