So it has been a few days since I was at the conference and I came across a few companies and products that I have not have the opportunity to see.
One of the products that caught my eye was Darktrace they sell their product as the “Enterprise Immune System” essentially they are smashing Big Data and network analysis together to get a picture of what is normal on a network and what is not.
The company was started by mathematicians from the university of Cambridge and former Mi5 works the company is based out of the U.K
I had the opportunity of speaking with 2 of the reps at the conference and they were very knowledgeable about the product.
they were very willing to share info on the product and have kept in touch with me since after the event which is always good.
So what is Darktrace?, Darktrace is a device that sits on a span port or network tap preferably on the core and it listens to all the traffic that passes through the core to get an analytical view of what happens on the network.
Under the hood there is some advanced mathematical algorithm that is used for the analysis the system records things such as URL’s and requests out to the internet this is a wonderful tool in security since things such as Malware infections can be flagged when they perform certain calls out of the network for certain URLs or files that have never been seen on the network. This can help detect unusual activities this is a concept known as machine learning which the system heavily uses to perform these tasks.
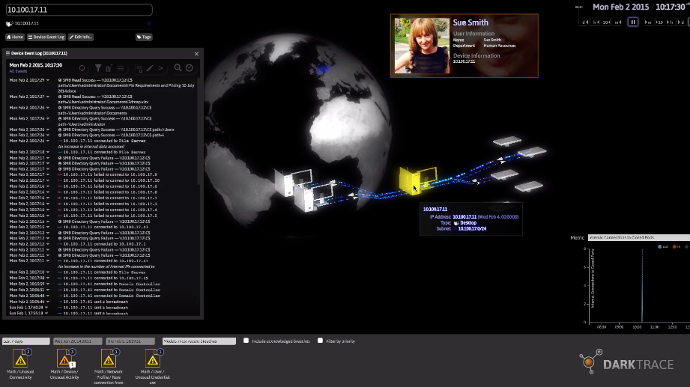
The User Interface looks like something out of a Scifi movie
This is the future of security we need to embrace predictive analytics and machine learning to really listen to what is going on in the network every detail is important and Darktrace is right up there at the forefront of the new age.
The legacy approach is not as effective as it once was things like ransomware and APT are becoming some advanced so quickly it’s going to take more than just the usual to stay ahead of the game.
I spoke with a rep from Darktrace and she provided me with a play by play article on how Darktrace was able to help an online casino secure their after a ransomware breach see the article here https://threatpost.com/diary-of-a-ransomware-victim/117877/
Also, they provided me with an awesome white paper on their automation and machine learning technology
My thoughts
A company built by spies and mathematicians? sweet
On a serious note, this product and those like it are the future of security more and more vendors are releasing products based on analytics instead of traditional solutions.
Darktrace has a very informative team and website with all sorts of case studies and the facts speak for themselves more and more threats are flying around the internet that has been caught first with analytics and machine learning.
Here is a link to a page of whitepapers from Darktrace https://www.darktrace.com/resources/
As I have mentioned in previous posts Big data + security is the future and I am happy to see solutions coming out that embrace this new era of security
The only issue I see is the behavioral analysis and I have recently sent this question into Darktrace so I am waiting for an answer.
my concern is what happens when I bolt this solution into my network that has already be compromised ?. Will that traffic be white-listed and considered as normal? what happens if a comprise happens during the data gathering stage will that also be seen as normal?
I am waiting for an answer on that I will update this post when I get it
-Update check the comments for an answer to the above question

Hi Sean,
I’m a representative of Cyberseer – an official partner of Darktrace providing managed services for them. The below should help with your questions:
Perfect data is not needed. Darktrace leverages two different approaches to detecting anomalies: comparing each device’s behaviour to its own history, and comparing devices to their peers. This peer comparison allows us to avoid learning existing bad behaviour as normal because compromised devices will exhibit behaviour different to their immediate peers.
So if your network was compromised before work commenced, a pre-existing intrusion would be discovered as anomalous in comparison to the normal behaviour of similar devices.
If you have other questions, the Darktrace FAQ’s on our website may be useful: https://www.cyberseer.net/cyber-security-solutions/technology/darktrace-cyber-intelligence-platform/darktrace-faqs/
Thank you for the info !
I was contacted earlier by Darktrace just didn’t get around to updating the article